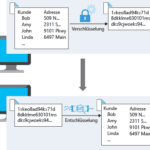
- Kerberos: This validation protocol provides robust authentication for client-server-based applications through encryption with secret keys. Kerberos assumes that all endpoints within a network are insecure. It therefore enforces strong encryption for all communication and all data at all times.
Dieser Beitrag ist auch verfügbar auf:
![]() Deutsch (German)
Deutsch (German)