Office 365 Message Encryption (OME) is a service built on top of Azure Rights Management (Azure RMS) that allows you to send encrypted emails to people inside or outside your organization, regardless of the email address. Destination address (Gmail, Yahoo! Mail, Outlook.com, etc.).
As an administrator, you can set up transport rules that define the conditions for encryption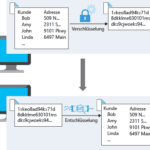

To view encrypted messages, recipients can get a one-time identifier, sign in with a Microsoft account, or sign in with a work, school, or college account associated with Office 365. Recipients can also send encrypted replies. You don’t need a Microsoft 365 subscription to view encrypted messages or send encrypted replies.
Image source: https://jaapwesselius.com/2019/09/27/office-365-message-encryption-ome/
Dieser Beitrag ist auch verfügbar auf:
![]() Deutsch (German)
Deutsch (German)

