“End-to-end encryption” (Peer-To-Peer Encryption)
Encryption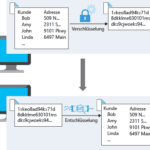
Licensed under CC-BY-SA 3.0 Germany (http://secupedia.info/wiki/SecuPedia:License)
Here, data is encrypted before transmission and decrypted after reception.
The sender and recipient are connected to each other equally, which enables secure communication.
Source: https://www.secupedia.info/wiki/Ende-zu-Ende-Verschl %C3% BCsselung # ixzz6qUl7LAQa
Image source: https://medium.com/@simpledex.org/peer-to-peer-end-to-end-encrypted-conversations-are-they-really-private-1c9510b08f62
Dieser Beitrag ist auch verfügbar auf:
![]() Deutsch (German)
Deutsch (German)

